A good number of users go on the web through a Local Area Network (LAN). All devices on a LAN tend to share a common communications line or a direct link to a specific server. This network is usually for a limited number of people or devices.
The internet available on a LAN is accessible through a wired cable or a wireless setup (router, for example). The wired connection has the advantage of being significantly faster and being less prone to interferences, but it lacks the flexibilities that come with WIFI connectivity.
When you attempt to connect to the internet, your ISP (Internet Service Provider) assigns a specific IP (Internet Protocol) address to your computer (if it has a direct connection to the LAN) or to your router (if your devices are on the web through WI-FI). With this piece of information, you are easily identifiable.
Pro Tip: It is possible to fix many PC issues by using the PC Repair tool. PC Repair is easy to use and reliable Windows optimization software developed to fix hundreds of system issues.
Special offer. About Outbyte, uninstall instructions, EULA, Privacy Policy.
If you visit a website or run apps that use your internet connectivity in general, their servers see and record the entirety of your activity with them. An IP is what gets attached to you when you try to use the internet.
If we considered the concept of an IP in the real world, it is similar to items like the driver’s license number you get if you want to drive or even the name your parents gave to you since birth that everyone uses to identify you. Surely, you would not want the details that distinguish you from others visible everywhere. So why would you consider a different rule for your IP address?
Here is a short list of details discernable from a visible IP address:
- Country
- Region
- City
- ZIP code
- Longitude and latitude
IP addresses are 4 strings of numbers. For example, 123.456.789.0. They are not random, far from it. An internet organization manages and allocates the block of numbers that make up the Internet Protocol. We have run out of addresses under the IPv4, but the world came out with the IPv6 to address this shortage and other shortcomings associated the older system of IPs.
If you could somehow hide your IP address, people who intend to trace you or obtain information about your activities would find it very difficult. In theory, you cannot make your IP address go away—it is borderline impossible to connect to the internet without it. Even if you somehow manage to do so, your success would not last long. So, such an operation is a waste of effort and time.
What you can do is to obscure the actual information or existing details to make sure they differ from the real thing. For example, VPNs allow users to spoof their physical location. We will discuss these things later in this guide with more details.
There are many reasons you would want to stop other parties from knowing your IP address when you are on the internet. In fact, due to the weight of the arguments in favor of staying anonymously online, we recommend that you hide your IP address.
Here are some of the top reasons for which you should hide your IP address:
Your privacy is important:
If you want to stay anonymous online, then one of the most critical things you must do is to hide your IP. Your browsing history, habits, choices, views and so on are yours and should remain private. After all, these details form part of your personal information which can always be used against you if the need arises.
Do you often see those annoying ads displayed on your screen about people looking to mingle in your city? Well, such occurrences are not a coincidence. Advertisers can do this by targeting you. In fact, they can figure out where you live, or they could also know that you are single. Remember that your IP is visible. Cookies also help ads do creepy stuff like this though.
To remain safe:
If your IP address is hidden, hackers and other cybercriminals cannot take advantage of it. For example, if criminals know your home address, they can track you and even visit you. Not that you would like to hear it, but online tracking is possible if your IP address is not secret.
We would like to assume that you are not doing anything illegal on the internet. Thus, you might believe that you have nothing to fear since you are not going to anything wrong, but this could not be farther from the truth. Cybercriminals do exist and are always looking to take any form of advantage available against their victims. Even the smallest bit of information would help them.
If you often discuss sensitive subjects on a forum, for example, then using a hidden IP is not a bad idea. If you frequently connect to public WI-FIs and use the internet on these networks to access a lot of things, then the use of a VPN is very much in order.
Nobody is encouraging you to break laws because you believe the authorities cannot trace you. However, keeping your IP address hidden is a good defensive tactic for most intents and purposes. A VPN, for example, protects you far more than you could imagine.
Elimination of restrictions or blockages:
Many services and content are often restricted to certain geopolitical zones or countries. Since your IP address is used to determine where you are browsing the internet from, you can hide your actual address (or use the one located in the favored zone) to get access to stuff that would otherwise be denied to you for debatable reasons.
For example, the BBC provides streaming services for excellent content and restricts it to users in the UK. If you want to access such videos and other items, all you have to do is connect to a VPN server in London or use a proxy server based in the UK to make it appear that you are coming from somewhere in the country where BBC originated.
Most users want to watch videos on Netflix, but this firm offers services that vary a lot by country. In fact, Netflix actively tries to block VPNs to prevent people from using them to circumvent their policy. Virtual Network Providers are winning the war though as they keep on finding a way to stay ahead of Netflix efforts.
Some ISPs themselves also stop users from using their bandwidth to access certain content. For example, Torrent downloads are not possible on some networks due to such restrictions. Well, some people believe that if they pay for a service, what they do with it is entirely their own business. If you think like those folks, then the use of a VPN is your best bet if you want to get your money’s worth from your ISP.
Piracy and illegal operations:
Although we do not endorse participation in criminal activity, we cannot exclude it from the list of reasons some users decide to hide their IP. Many countries have strong piracy laws to prevent illegal sharing or downloading of content on the internet. In fact, the government administrators for the web in some states actively block a good number of sites suspected to be harboring illegal or harmful material.
Even if you are involved in piracy and other shady operations instead of noble activities, a VPN cannot discriminate in its effort to protect who you are. Besides hiding your IP address, a Virtual Private Network will disguise your uploads and downloads.
How to hide IP address on Local Area Network
Internet technologies have gotten better over time, and these days, it is not difficult for an individual to access the internet anonymously with a hidden IP. We will explore almost all the possible means by which you can hide your IP address. We will also explain how they work, rate their effectiveness, state the advantages and downsides associated with them, and so on.
Use a VPN:
A VPN (abbreviation for Virtual Private Network) provides the most reliable and convenient way of surfing the web anonymously and at the same time remaining safe. In recent times, as more people started to exercise some degree of control over their privacy, the popularity of VPNs have skyrocketed.
A VPN works by encrypting a user’s internet connection and connecting the user to the web through a private network via a secured tunnel. The user, instead of connecting to the internet directly, transfers and receives encrypted data from the VPN server.
If you use a VPN, even your ISP cannot see what you do on the internet. At best, your Internet service provider can only see that you are connecting to a private network and nothing else. Also, the websites you visit would end up having useless or no information about you.
Many individuals use a VPN to watch movies on Netflix that are not available for them in their resident country. Movie streaming sites often discriminate against which users in several geographical locations they provide with their content. Users employ a private network to help them appear as if they are coming from a non-restricted nation.
Performance issues form the bulk of the downsides associated with the use of a private network. The internet speed (download and upload) you get while you are using a VPN are lower than the possible figures you see when you connect to the internet directly and do a speed test.
These issues are a result of the VPN having to encrypt your data and transmit it to the private network to process your request. The Virtual Private Network does its job, then sends back this information to your VPN client, and finally, the private network carries out the decryption process of the received items.
Surely, you can see that these operations are tedious. You can also understand why or how they require a lot of time. Fortunately, as there are now many VPN firms, you can choose an excellent provider of private network service to limit the downsides or performance. Remember that the best packages are not free and would set you back some money.
Use a Proxy:
Browsing through a proxy is probably the easiest way of hiding your IP address online. Proxies are not as robust as VPNs regarding their operations, but they provide a stable platform for users to surf the web with a different IP address. A proxy server works as an intermediary between a user’s PC and the internet.
In simpler words, the proxy—a user connects to—makes requests to websites, servers, or services on the internet on behalf of the individual involved. After the proxy processes the data, it presents the information to the user who initiated the whole process. Therefore, the visited site sees the proxy server’s IP as the initiator and receiver. This setup protects the identity of the individual.
Proxies can hide a user’s IP if they are set to do this. They appear to sites as a user agent that differs from that of the person using them. They can also save or reject cookies, but they do not transfer them to the user’s computer. All these changes and alterations try to ensure the anonymity and privacy of the people using a proxy.
Although many individuals use a proxy server to access restricted content and stay anonymous online, some firms and institutions set up proxies on their networks to limit the internet activities of people using their service.
Proxy servers make many other operations and setups possible, but since we are focusing on the ones with direct benefits to users, we will not go into them in details. For example, religious companies or schools might enforce a ban on adult sites so that their employees or students cannot gain access to adult content within their environment.
Proxy servers offer almost all the benefits that a VPN provides except for encryption. Users may also suffer more performance downgrades with a proxy. Bandwidth speeds are even lower. You must also be very careful with your choice of proxy servers or websites.
A rogue (or infected proxy server) can inject viruses or other malicious items into your computer. Since proxies have a certain level of control over the response you receive, they are very much capable of altering them. Sometimes they make bad changes if attackers have configured them to do so. Therefore, proxies are a good option only if you are not dealing with sensitive data.
Also, a proxy server keeps logs of users’ activities. This fact presents a significant downside for people who were looking to keep information about their activities from everyone in the first place. The saved data can always be used against you if the need arises.
Beware of public proxy servers and free proxy services in general. If you are using one, remember not to engage operations associated with the sending and receiving of personal information. Paid proxy servers are better regarding handling sensitive details.
The other significant problem associated with the use of a proxy comes up when the service is rendered ineffective. There are some websites set up to counter the mirroring effect that proxies employ to appear as if they were you.
When you are dealing with such sites, your IP might become visible, and of course, all the benefits that you are expecting or the ones that compelled you to use a proxy would disappear too. The restricted site would be able to enforce its laws on you.
We have established that proxies are not as good as VPNs, but that does not mean they should not be used at all. In fact, there are specific scenarios in which a proxy is the best choice due to the relative simplicity to set it up and use it.
You can set up your connection to use a proxy server far faster than you can download and install a VPN. There are also numerous free proxy sites, which you can quickly type in on the address bar in your browser. There, you can surf anonymously on the web or use a different IP address, and this means that the websites you are touring with the help of the proxy site cannot find out your actual IP.
Furthermore, if you are a Chrome user, you would have access to the multitude of proxy extensions available on the Store there. Be careful—developers market some of these add-ons as VPNs. Do not be deceived.
The vast majority of the extensions we described work similarly to proxies. Thus, the protection you get might not be as strong you would like, and the effectiveness of these add-ons might never reach the heights you were expecting.
Use a special browser:
The question of anonymity and privacy concerns has given momentum to the rise of browsers with built-in VPNs or proxies. The Opera browser, for example, is one program for surfing the web which has an embedded private network that users can turn on or off when necessary.
There is also a browser called Tor (abbreviation for The Onion Router), which went multiple steps further to ensure the highest levels of privacy and security. To be honest, this program is far ahead of all its competitors. Well, that is even if competing services that offer a similar level of protection and functionality exist. We will focus on Tor here.
When data passes through the Tor network, it goes through randomly selected Tor relays, and in the process, this data is encrypted and re-encrypted many times. The routing itself is not visible as result of the encryption activity.
Even if an organization or a ridiculously powerful person somehow manages to intercept your traffic at the entry or exit points between the nodes, they would only be able to figure out the previous and the next jumps. They would still not be able to find out where exactly the chain started or where it ended up.
Tor uses the best tools and means to hide your IP, encrypt your connection, and so on. There are other things it does to protect you like its use of DuckDuckGo search engine (instead of Google), which may seem minor to you, but they go a long way in ensuring that your identity is not compromised.
People living under an oppressive regime, journalists in dangerous zones, and other categories of people—who need to transmit or receive sensitive details or information— and at the same time need to avoid giving away their identity—find Tor to be an invaluable resource. Note that the key here is anonymity and protection. In case you failed to notice, these terms have appeared a lot in this guide.
Even if you are not a top military official—on a dangerous assignment in an alien country— who wants to browse the web, you should still use Tor for if you need to go past restrictions or internet censorship. It will also help you keep your internet activities out of the prying eyes of advertisers, ISPs, websites, government agencies.
Because Tor has many capabilities or functionalities, its use is also prone to abuse. The Tor network can support things far more complicated than anonymous and secured browsing. It can host sites through its secret services. Of course, only Tor users can access them.
Tor is only as reliable as the user handling it. We mean that if your adversaries want to get to you, they are more likely to be successful if they exploit your shortcomings or vulnerabilities peculiar to your individual. Well, it is also possible for them to find security flaws in the Tor browser application (if you are not running the latest version) but the network itself is far more resistant to attacks.
There are very few downsides associated with the use of Tor. Besides the slower internet speeds problem, which everybody expects given the complexity of the service and the level of protection it offers, there is not much to consider as disadvantages of using it.
Maybe we can go with some minor performance issues like your plugins not working correctly, flash not loading at all, and so on, but we consider these things too trivial to discuss. After all, these add-ons can compromise your security very quickly, and most people who want what Tor offers are hardly bothered about the loss of those things.
Although all is well and good for most normal Tor users, some people care about the abuse of the service despite the fact that it does not affect them. Or maybe it does, morally at least. Unfortunately, not every Tor user out there is seeking to use the service for self-protection or use it to do good things. Cybercriminals, like Human right activists, also use the network.
For example, some people use the hidden site service to create something like The Silk Road, which was set up to traffic drugs. People engage in other sinister activities like child pornography through Tor. Some categories of users abuse the network to trade arms. We long decided not go into details about these things, but we just felt that it was fair you knew about them.
If you wish to employ the maximum level of protection and security on offer, you should set up a VPN, then still try to use the Tor browser. This combination is as formidable as it gets when it comes to securing your anonymity online. It would be incredibly difficult or borderline impossible for your adversaries to figure out your real IP address
Reset your IP:
The final method we are going to examine is several levels below the rest if we consider the degree of convenience it offers and its effectiveness. Here, you are going to hide your IP by resetting (or changing) it. This method is applicable only to users with systems running Windows. It is useful if you got blocked or banned from websites or services on your current IP.
Follow these instructions:
- Ensure that your internet connection is active on your PC. Now open a Command Prompt window with administrative powers. If you are running a recent version of the Windows operating system, you can do this by right-clicking on the Windows Start icon and selecting Command Prompt (Admin) to launch the required program
- Here are the instructions for users running older iterations of Windows: press the Windows button on your keyboard or click on the Windows Start icon. Type cmd into the available text box to perform a search. You should see Command Prompt on the list of results. Right-click on it and select Run as Administrator to open the needed window
- After the window opens, type in the following lines of command (one at a time) and press the Enter key after inputting each one:
- ipconfig /release
- ipconfig /renew
- If Windows carried out the operation above successfully, you must restart your system and router to let the changes take full effect. Finally, after the reboot, you should get a new IP.
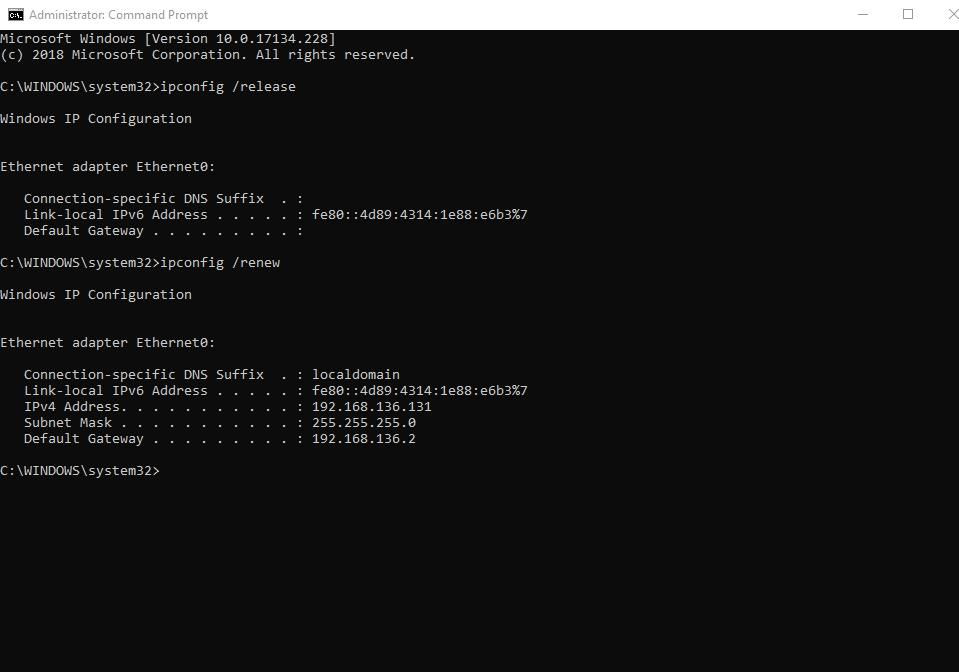

Note that the success of this operation is dependent on the policies your Internet Service Provider (ISP) has in place regards the changing of IP addresses by its customers. They probably would not allow you do it very frequently.
If your Internet Service Provider did the static IP set up for you, then the method above would probably fail to help you change your Internet Protocol Address. You will have to contact your ISP and ask directly for a new one.
Sometimes they might agree to your request, and other times they might call your bluff. If you got refused and you believe getting a new IP is worth it (especially a static one), then you should consider changing your service provider.
It is time we spelled out the difference between privacy and anonymity. After all, both terms appeared numerous times in this article. They are different things. You must know that is incredibly difficult to browse the internet privately and anonymously at the same time.
For example, a VPN—even with all its powers of encryption and manipulation of proxies—cannot fully ensure your anonymity. A VPN cannot remove all forms of identification. You would have to play your part if being unidentifiable is vital to you. Only you can protect yourself by not entering your names on websites and forms, and so on. Take note of other similar guidelines.
We hope that you are running a reputable antivirus to secure your system and protect you from the vast majority of threats that might find their way to your device. We also recommend that you download and run an excellent antimalware program like Auslogics Anti-Malware to provide that extra layer of protection that comes in handy if anything ever gets past your main security application.

The recommended anti-malware program works well with the vast majority of antivirus brands and does not interfere with their operations. Therefore, the downsides to the combination of such robust security programs are limited. Furthermore, this setup protects you better than the previous one.
It is easier for a VPN to help you achieve the privacy goal. The service prevents everyone from tracing your actions on the internet back to you. These actions vary from simple things like those embarrassing web searches to the more complicated illegal Torrent downloads.
There are perfectly valid reasons you would want to hide your IP address, and the act has become easier to try out in recent times thanks to the many techniques, apps, and services that can help you do it. Just go with the one that suits you best and finally, you are free to enjoy your stay online without the fear of your identity becoming visible.